<< back
8 August 2020
An Even Nicer Picture
Challenge Source: Defcon 28 - Red Team Village CTFChallenge Category: forensics
Forensics - An Even Nicer Picture
Trying the same method from the “A Nice Picture” challenge first:
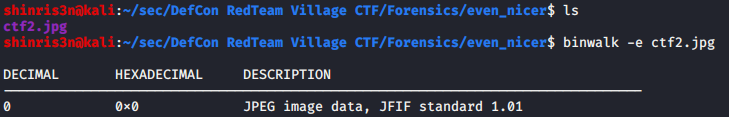
There doesn’t appear to be anything inside, but the file is clearly even larger than the first, identical picture, so let’s see what else we can do. Exiftool doesn’t reveal anything in the metadata, so how about Steghide?
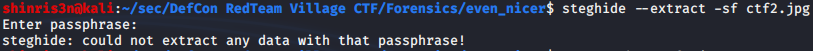
Nothing appears to show up, but maybe there’s a passphrase. Using a tool called Stegcracker (installed via pip3; defaults to using /usr/share/wordlists/rockyou.txt):
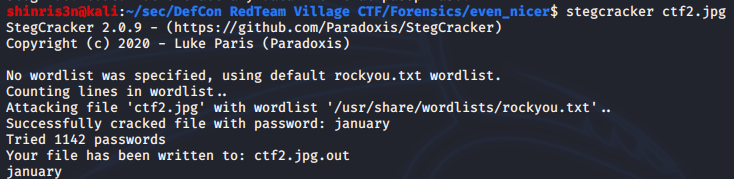
Inspecting the output:
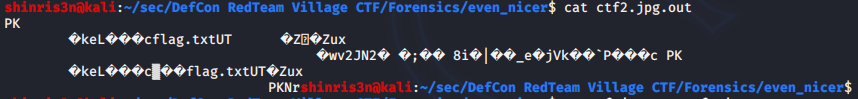
Since the file starts with PK, this is a zip file. So we rename it and try to open it up, finding that its password protected.
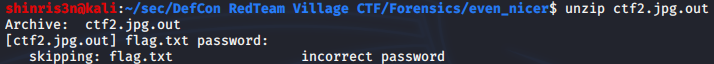
This part is actually the exact same as the “A Nice Picture” problem (including the password), but running through the steps again, we can use fcrackzip using rockyou.txt as the wordlist here as well: