<< back
8 August 2020
Clicker
Challenge Source: Defcon 28 - Red Team Village CTFChallenge Category: pwn
Pwn - Clicker
“All you have to do is score 10,000,000 to get the flag. Get Clicking!!!!!”
First we download clicker and make it executable.
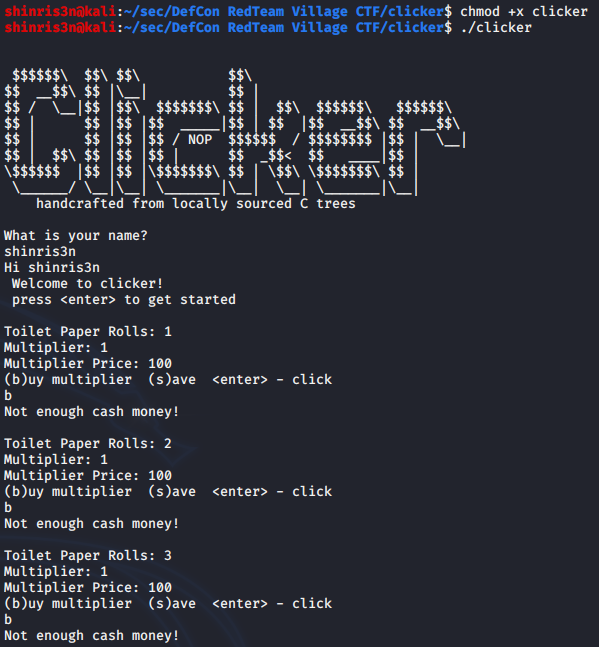
Well we can hit or hold enter to buy toilet paper and buy a multiplier once we have enough rolls. This resets the number of rolls to 0, and then we can buy 2 per “click”. Yep, there’s no way we’re getting to 10 million like this.
So what happens when we save?
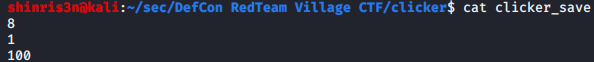
Just text? That seems easy enough to mess with!
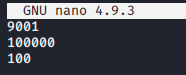
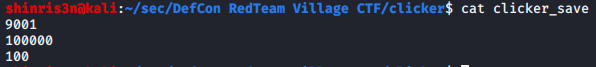
And then after messing around enough we realize there’s no way to load actually it, so this was likely a troll…
So how about gdb?
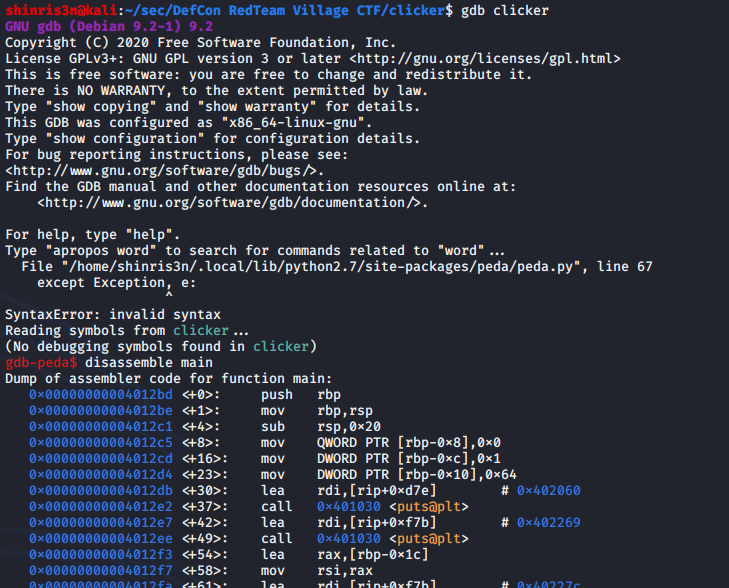
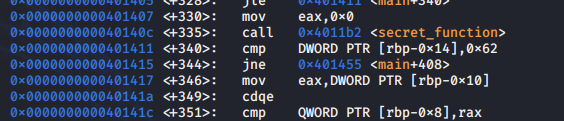
Scrolling through, secret_function sure looks interesting. So lets run the program, then ctrl-c to break during execution:
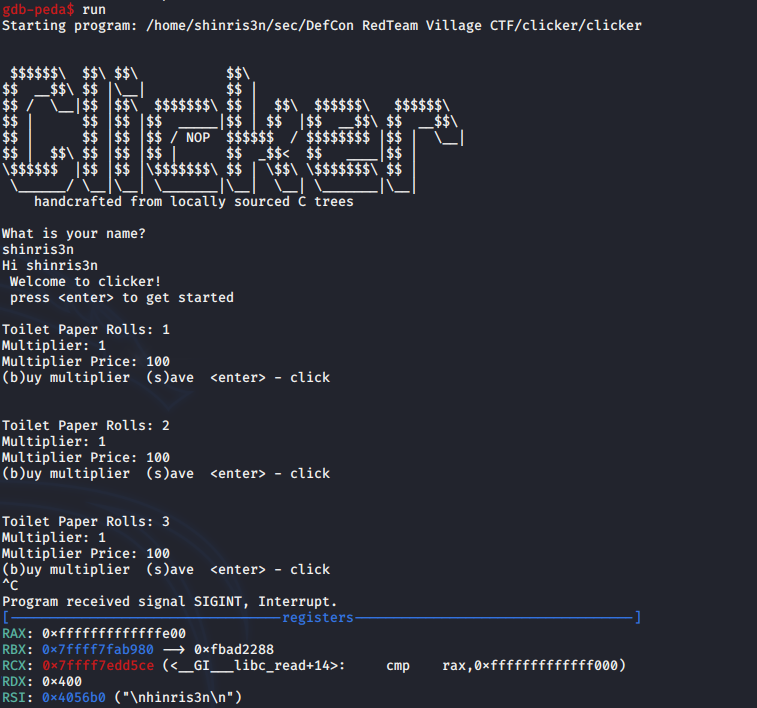
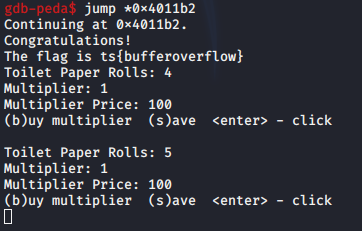
Now lets try to jump to the secret_function and see what happens: