<< back
14 April 2020
2048
There were a couple of hints upfront to get you started:
-
2048 is a puzzle game where you keep combining pairs of tiles.
-
The challenge text was a b64 encoded message that decoded to something to the effect of “plzhelpme”.
Since the attached file was a large encoded message, with the hints given it was safe to assume that the flag was b64 encoded over and over again.
A Python3 script can be written to solve this:
import base64
with open('2048') as b64file:
b64input = b64file.read()
decoded_output = base64.urlsafe_b64decode(b64input)
print (decoded_output)
iterations = 1
while iterations < 50:
decoded_output = base64.urlsafe_b64decode(decoded_output)
print (decoded_output)
print (iterations)
iterations = iterations + 1 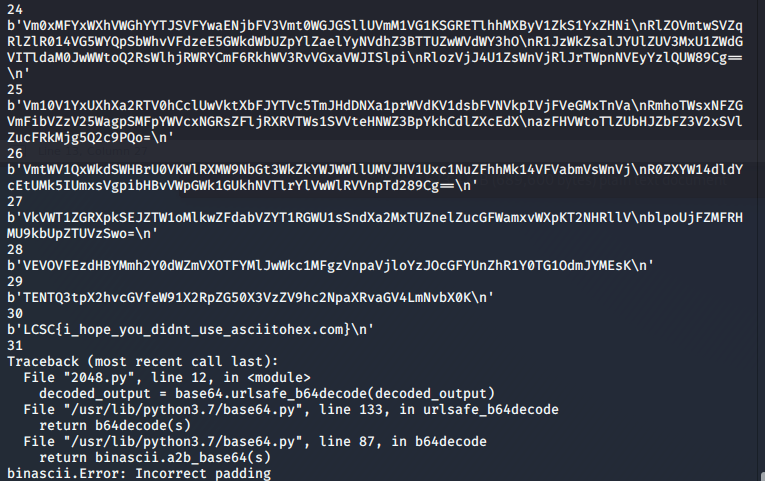
Alternatively, CyberChef is a great resource for problems like this.
Using a loop in CyberChef and loading the file as an input:
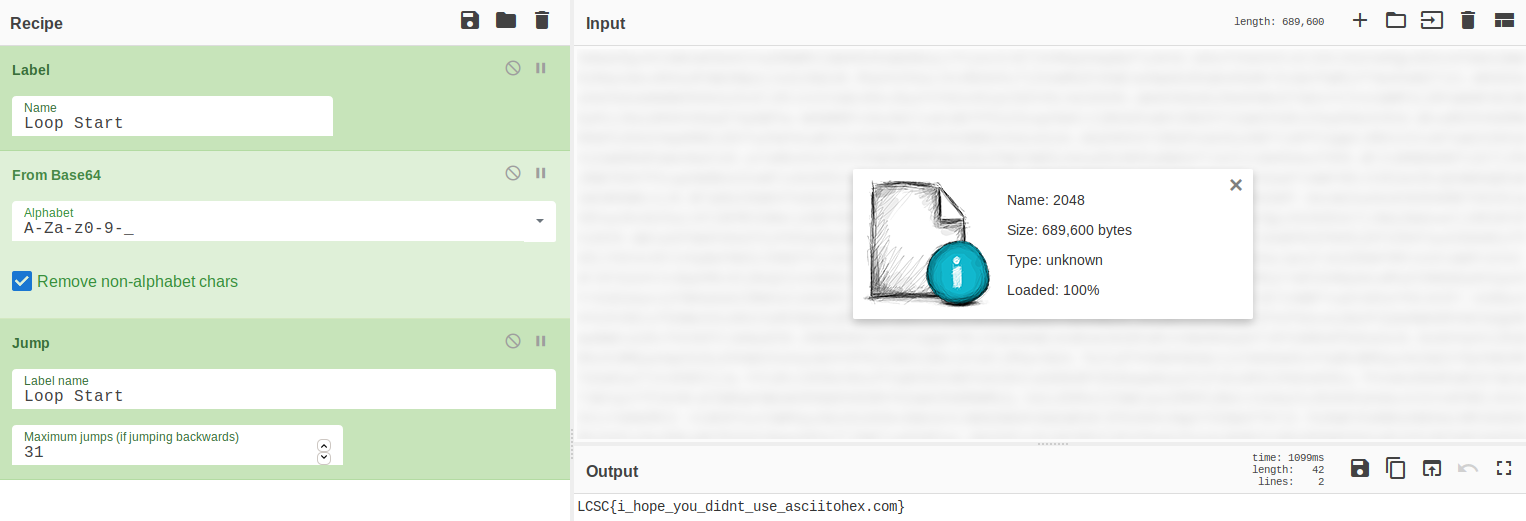
As a side note, there’s a function called “Magic” in CyberChef that works really well if you don’t know the encoding, or different types were utilized. It didn’t work for this problem, however, probably because of the depth.
Tags: VirSecCon, ctf, scripting
